Due to the recent Apache Log4j2 common vulnerabilities and exposure (CVE), Salesforce Data Loader users will need to re-install desktop app. This is not to be mistaken for Data Loader IO.
The December, 2021 (API version 53) from Salesforce resolves the security breach, and will better protect your org from hackers. The below information can be used by administrators for
making this critical update. Installing data Loader and other Java considerations – link
Begin by uninstalling the older version of Data Loader from your Mac or PC. Then follow these steps for Installing to the latest version of Data Loader (API v. 53.0.2 or later). Version 53.0.01 doesn't cover several CVEs.
Log into your Salesforce org.
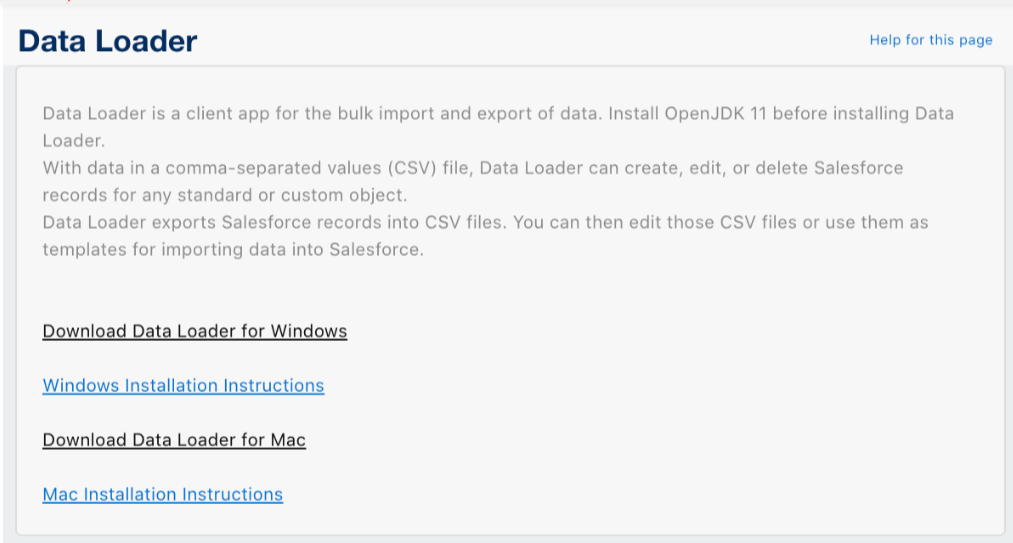
Go to Setup > Data Management > Data Loader to see this screen with links: (downloads folder) or get it from GitHub – link
If this isn't available from the Setup menu, then the profile does not have access to Data Loader.
The CVEs do not affect JDK directly according to Azul's site – link here. So reinstalling JDK is not necessary.
Below is a video on how to install Data Loader for your MAC or PC:
These steps do not completely protect your org from Log4J2 attacks. I would recommend that your administrators regularly check over your org's Flow Application Error, Apex Errors and other system automated logging email notifications. If you see suspicious inputs for failed processes with a string such ${jndi: where it doesn't belong, then you know there's a vulnerability that Salesforce is yet to resolve (or doesn't know about). Opening a case with Salesforce will help bring attention to that security threat. Guest User licenses and other unauthenticated users are also avenues would-be hackers have used in their attempts to hack Salesforce orgs.